A common concern is how to address the issue of devices bypassing network controls by making local network changes on the device. The most obvious answer is to prevent those types of changes on the device. That being said, that’s not always possible for a network administrator (i.e., maybe you don’t own the device).
To combat this, we turn our focus to the network Firewall. You might have this as a separate appliance on your network or, more likely, it’s part of your router appliance. Regardless of where it sits, you likely have a network firewall and we can use that to create rules to control outbound requests.
This article will focus on how to prevent local bypass attempts by network users that try to manipulate their device settings. It will show you how to use a firewall to explicitly allow and block DNS specific traffic on a network. This example will use the Unifi DreamPro machine, but the principles and examples shown should be similar to what you find in other Firewall applications.
Video Tutorial Using the UniFi DreamPro Appliance
Block DNS Resolvers On a Network
Step 1. Log into your Firewall / Router
Every router is different, log into yours.
Step 2. Navigate to the Network Firewall settings.
Depending on your device, this can be anywhere but often found in the main navigation (possibly under ‘Security’).
In the Unifi DreamPro OS you will see something like this:
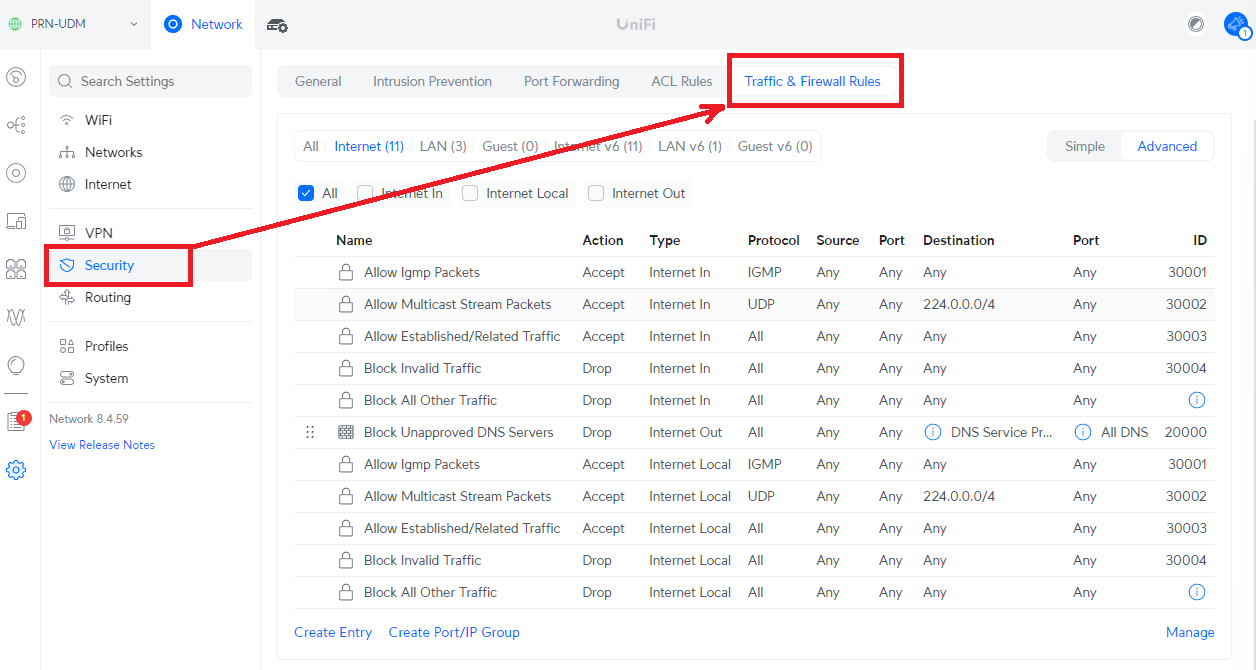
Step 3: Create Two Outbound Entries
What you’re looking to do is create two rules that control what is and is not allowed on your network.
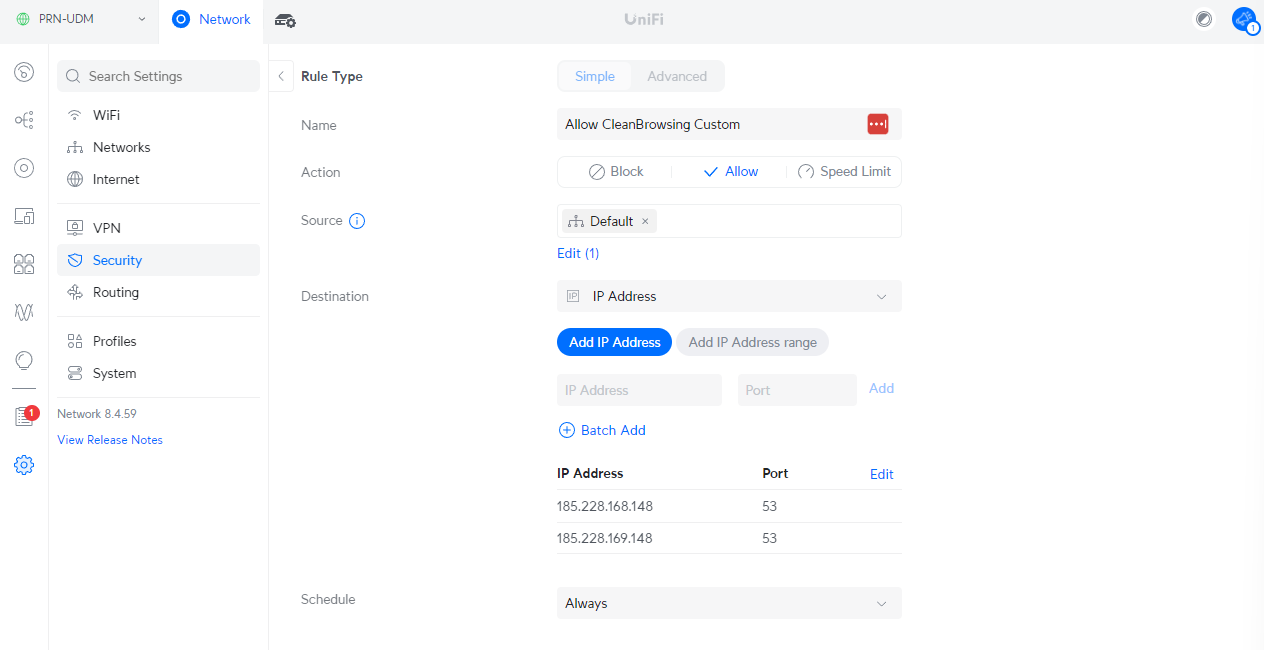
Allow CleanBrowsing DNS Resolver
Via the DreamPro console you have the option to create simple and advanced rules.
Using the simple rules, create an entry that looks like something like this:
| Action | Allowed |
| Source | Default Network |
| Destination | Include your preferred Resolver Address (e.g., CleanBrowsing) |
It will look like this:
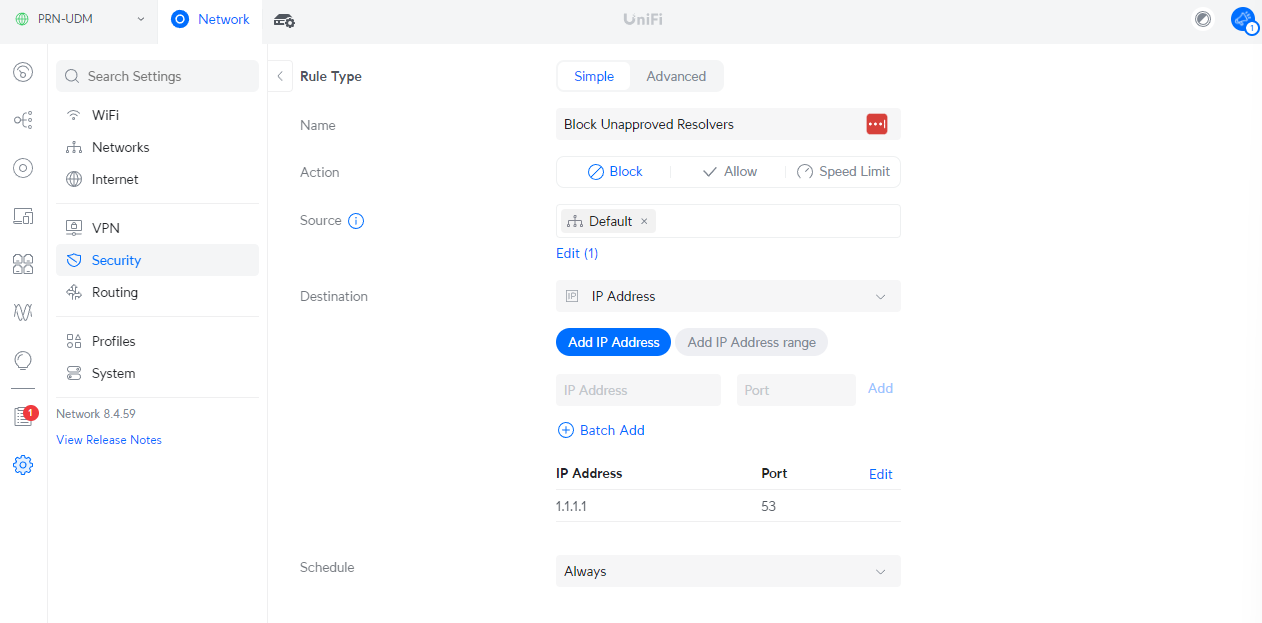
Block Unapproved DNS Resolver
Now we create an outbound rule that blocks DNS queries that are not using our preferred resolver.
Using the same Simple interface, we do something like this:
| Action | Block |
| Source | Default Network |
| Destination | IP Address Example: IP Address: 1.1.1.1 Port: 53 Enter all the DNS resolvers you want to block. We provide a list of common resolvers below. |
It would look something like this:
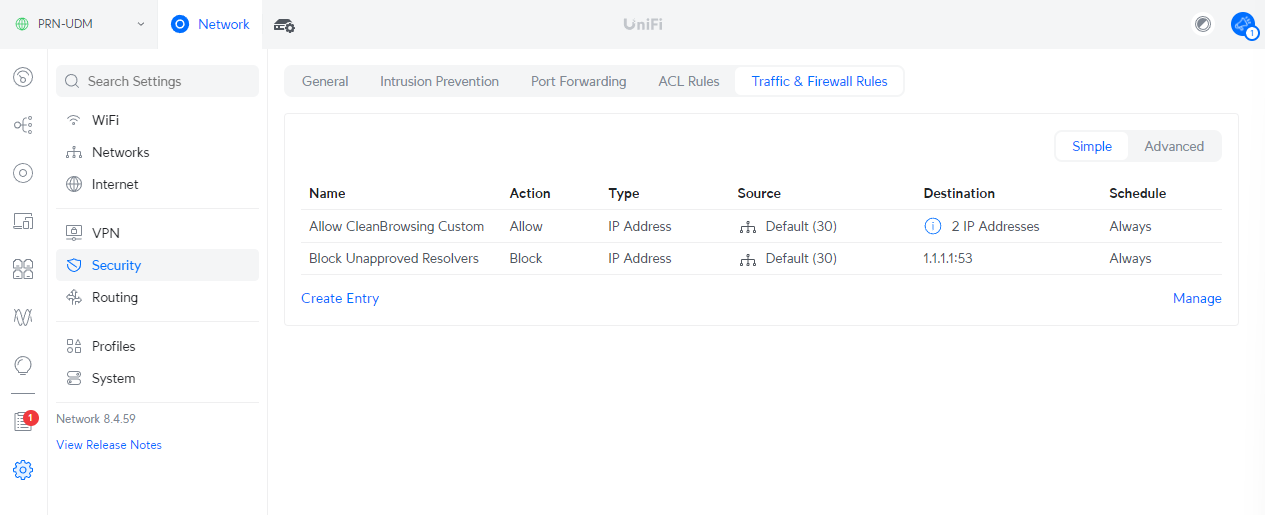
When it’s done it will look something like this:
Additional Information: Commonly Used DNS Resolvers
Here is a quick list of commonly used DNS resolvers and their corresponding IP addresses:
| Provider | Primary DNS | Secondary DNS |
|---|---|---|
| 8.8.8.8 | 8.8.4.4 | |
| CloudFlare | 1.1.1.1 | 1.0.0.1 |
| OpenDNS | 208.67.222.222 | 208.67.220.220 |
| Quad9 | 9.9.9.9 | 149.112.112.112 |
| Comodo Secure DNS | 8.26.56.26 | 8.20.247.20 |
| Level 3 | 209.244.0.3 | 209.244.0.4 |
| Verisign | 64.6.64.6 | 64.6.65.6 |
| DNS.Watch | 84.200.69.80 | 84.200.70.40 |
| Yandex DNS | 77.88.8.8 | 77.88.8.1 |
| Neustar | 156.154.70.1 | 156.154.71.1 |
