A Virtual Private Network (VPN) is a tool that helps users hide their internet activity and protect their privacy. It creates an encrypted connection between a user’s device and the internet, making it harder for anyone — including network administrators — to monitor or filter their traffic.
🛡️ CleanBrowsing: Internet Safety Made Simple
Filter harmful websites, block adult content, and protect your entire network. All with fast, privacy-respecting DNS.
Start Filtering Here →What is a VPN?
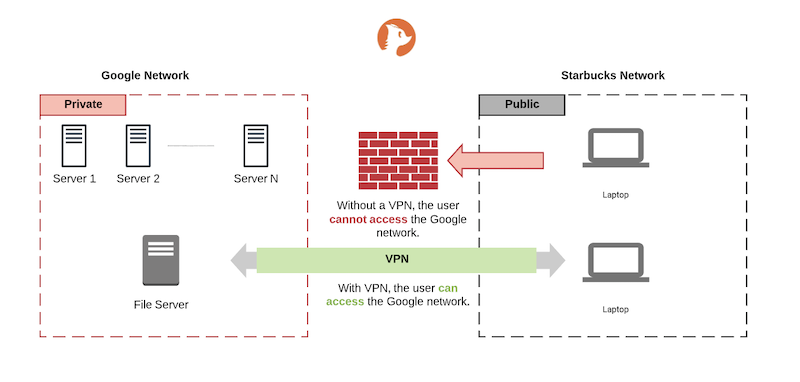
A Virtual Private Network (VPN) creates a private, encrypted tunnel inside an existing network. It allows a user to open a secure connection to the outside world — bypassing any network restrictions that may be in place.
Originally, VPNs were designed to allow users to securely access private company resources from remote locations.
However, over time, their use has evolved dramatically.
Today, VPNs are widely used for purposes far beyond corporate security, including:
✅ Circumventing network restrictions (e.g., school, corporate, or parental controls).
✅ Bypassing geographic restrictions (e.g., accessing streaming services like Netflix content not available in certain countries).
✅ Hiding browsing activity from network administrators and ISPs.
Because VPNs tunnel traffic outside of the local network’s control, they make it extremely difficult to enforce content restrictions or monitor activity, creating challenges for network administrators, parents, businesses, and even internet providers focused on building safe browsing environments.
How do VPN’s Work?
When a user connects to a VPN, their internet traffic is routed through a secure, encrypted tunnel to a VPN server. Here’s a simple step-by-step breakdown:
- The device connects to a VPN server.
- The VPN server encrypts the traffic and forwards it to the internet.
- The response from the internet returns to the VPN server.
- The VPN server encrypts the response and sends it back to the user’s device.
This encryption hides the original internet requests (like DNS lookups and website visits), making it difficult for anyone monitoring the network to see where the user is going or what content they are accessing.
Why Are VPNs a Challenge for Network Filtering?
VPNs encrypt user traffic, including DNS requests. This means that when a VPN is active, DNS-based content filtering solutions — like CleanBrowsing — may no longer see or control where a user goes online.
Even if you have DNS filtering in place, a VPN can:
- Hide websites that users are visiting.
- Circumvent category-based filtering (e.g., adult content, gaming, social media).
- Allow access to restricted content or apps.
Because of this, VPNs pose a significant challenge to anyone trying to maintain a controlled and safe network environment, whether in homes, schools, or businesses.
Challenges with Blocking VPNs
The biggest challenge with blocking VPNs lies in how they operate.
While services like CleanBrowsing can detect and block many VPN-related domains, there are scenarios where this is not possible — especially when a VPN:
- Does not rely on traditional DNS resolution.
- Bypasses device or network DNS settings by connecting directly to its own infrastructure.
In these cases, DNS-based filtering becomes less effective, because the VPN is actively avoiding or encrypting the very traffic a DNS filter would see.
Complicating matters further, VPN technology is now embedded directly into:
- Web browsers (e.g., built-in browser VPNs)
- Local devices (e.g., system-level VPN options)
- Standalone apps (e.g., mobile or desktop VPN clients)
Despite these differences in how VPNs are deployed, they still rely on a known set of protocols and ports.
Blocking these protocols at your network gateway can help significantly reduce VPN usage.
Here’s a list of common VPN protocols and the ports they use:
| Name | Description | Protocol | Port |
|---|---|---|---|
| PPTP | Point-to-Point Tunneling Protocol (PPTP) | TCP | 1723 |
| SSTP | Secure Socket Tunneling Protocol (SSTP) | TCP | 443 |
| L2TP | Layer 2 Tunneling Protocol (L2TP) | UDP | 1701 |
| IPSec | Internet Protocol Security (IPsec). | UDP | 500, 4500 |
| L2TP with IPSec | Layer 2 Tunneling Protocol (L2TP) with Internet Protocol Security (IPsec) | UDP | 500, 1701 |
| OpenVPN | open-source commercial software. It uses a custom security protocol that utilizes SSL/TLS for key exchange. | TCP, UDP | 1194 |
| IKEv2 | Internet Key Exchange version 2 | UDP | 500, 4500 |
| WireGuard | A new VPN protocol that is being widely adopted by VPN providers. | UDP | 51820 |
This is not a comprehensive list of the different port combinations, but it does show the most common options.
How CleanBrowsing Helps
CleanBrowsing includes a predefined VPN category that blocks access to many known VPN domains. We continuously update this category as new VPN services emerge to help prevent users from easily downloading or using popular VPN tools.
However, no DNS filter alone can stop all VPNs. Some VPN apps use dynamic IP addresses, direct IP connections, and custom tunneling protocols that can slip past DNS-based controls.
👉 This is why DNS-level VPN blocking should be seen as complementary to a broader VPN mitigation strategy, not a complete solution by itself.
What You Can Do to Strengthen VPN Defenses
In addition to using CleanBrowsing’s VPN category, you can take extra steps to limit VPN usage:
🛡️DNS filtering is essential — but it’s only one layer.
🛡️ Block VPN protocols (OpenVPN, WireGuard, L2TP) at the firewall.
🛡️ Monitor and restrict unauthorized apps — including VPNs integrated into browsers, antivirus software, and other encrypted technologies.
🛡️ Enforce strict device and network policies.
By combining DNS-based filtering with strong gateway-level controls, you can better protect your network and users from VPN-based bypass attempts.
VPNs are powerful tools that continue to evolve — and while they offer important benefits for privacy, they also create significant challenges for anyone trying to maintain a safe and controlled network environment.
DNS-based services like CleanBrowsing are an essential part of a layered defense, helping to block access to known VPN domains and services. But as VPN technology grows more sophisticated, relying on DNS filtering alone is not enough.
✅ By combining CleanBrowsing’s VPN filtering with strong gateway controls, port restrictions, and device management policies, you can create a more resilient network defense that significantly reduces the risk of VPN bypasses.
✅ The key is to view VPN mitigation as a multi-layered strategy, not a single control point.
Staying proactive and combining multiple defenses ensures that your network remains secure, predictable, and aligned with your content and access policies — no matter how users try to get around them.
🔍 Investigate DNS like a Pro with DNSArchive
Uncover historical DNS records, IP reputation data, and web metadata with one powerful tool. Built for threat hunters, researchers, and digital forensics teams.
Explore DNSArchive →