CleanBrowsing provides a DNS-based content filtering service, but like most DNS services it is limited by what is happening locally on a device. One of the biggest challenges is when a user makes a local DNS change. This article will provide a guide for those interested in mitigating this evasion technique.
This guide will be technical, and require some basic technical knowledge of networks and routers. A novice user can also do this, but it can cause a network to go off-line. This will be tailored towards a home user, but the technical concept can, and should, be employed by organizations (especially schools).
Domain Name System (DNS) & Local Settings
The most effective way to configure CleanBrowsing is deploy the service at the router. This allows the service to be applied to all devices connected to the network. There are instances where a local deployment makes sense, and should be considered complementary to the network configuration.
Regardless of deployment type, any administrative user has the ability to make changes locally to their device (applies to mobile, desktop and notebooks). These local settings will override the network settings by default, by design. It’s how network communication works.
While we recommend restricting what a user can do on their machine, that isn’t always possible. This is especially true in homes, libraries, and schools. To combat this challenge, network owners should restrict any changes on their network.
Local Network Changes
The most effective way to block local changes is at the edge of your network, specifically through the use of a network firewall. This won’t stop a user from making local changes, but it will function as a gate keeper to any activity on your network.
This means that if a user tries to change the DNS on a Windows machine to a non-filtered DNS service, while on your network, you will be able to intercept the change and reroute the traffic to your preferred DNS service.
Enterprises have network firewalls they can leverage for this, but for home users it is a bit different. Home users will have to make some changes to their home routers to make this work. For this article we’ll make use of open-source software to help a home user create thee same network experience you might find in a company network.
Introduction to DD-WRT
DD-WRT is an open-source firmware update that helps unlock your routers true potential. You will need to replace the software on your Router with this image, that’s where it can get tricky. If you are using an Asus router you can leverage MerlinOS, to achieve the same outcome. Merlin is built on DD-WRT and interfaces nicely with the ASUS routers.
Configuring Your Router
Before you get started, note that not all routers support DD-WRT but it is becoming more common. It is highly unlikely that the router your ISP provides, so be prepared to deploy a secondary router on your network. As you shop for potential options, spend some time looking at the supported devices. This will give you an idea of which router you should purchase.
This example will use a LinkSys WRT3200ACM router. We encourage you to stick with a router that has full documentation, and tested image for the specific router. This will be important to remove any potential variables through the installation process.
In our instance, it was relatively straight forward to install DD-WRT on our Linksys. We were able to do it via the GUI interface, under the Firmware update.
There are two firmware files to download and install. Do them both in this order:
Initial installation firmware (not needed for later upgrades): factory-to-ddwrt.img
Upgrade firmware: ddwrt-linksys-wrt1900ac-webflash.bin
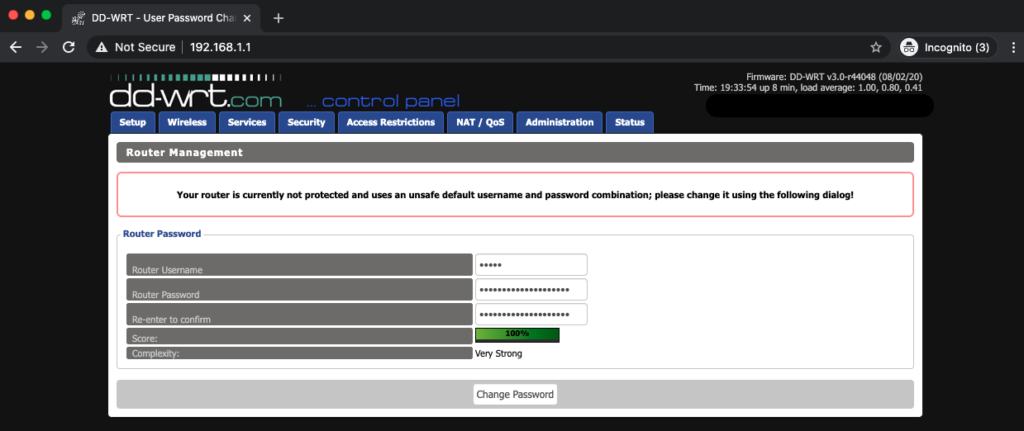
The first installation (factor-to-ddwrt) will happen in your Linksys dashboard. When the router reboots, it will greet you with the following DD-WRT page. This is where you will set your username and password to access the device.
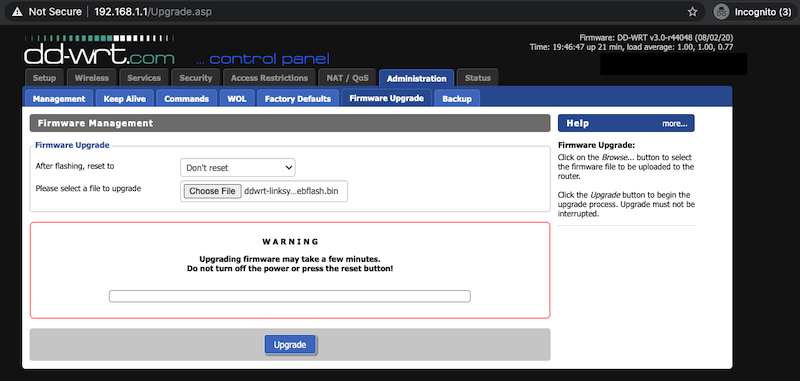
The next firmware image will be uploaded in the DD-WRT interface:
Once DD-WRT is installed, you can proceed with configurations.
Stop Local DNS Changes
With the router configured with DD-WRT we can move into configuring it to intercept all network DNS traffic.
Step 1. Basic Setup
Most of the initial configuration will happen in the Setup > Basic Setup page.
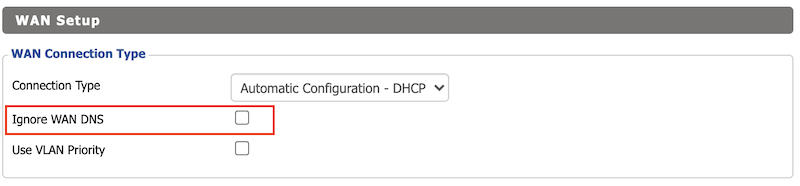
Disable Ignore WAN DNS setting in the WAN Setup section.
Scroll to the Network Address Server Settings (DHCP) section. Update your Static DNS entries with your preferred DNS. In our case, we’re using one of our customer filters, but the same applies for our free filters.
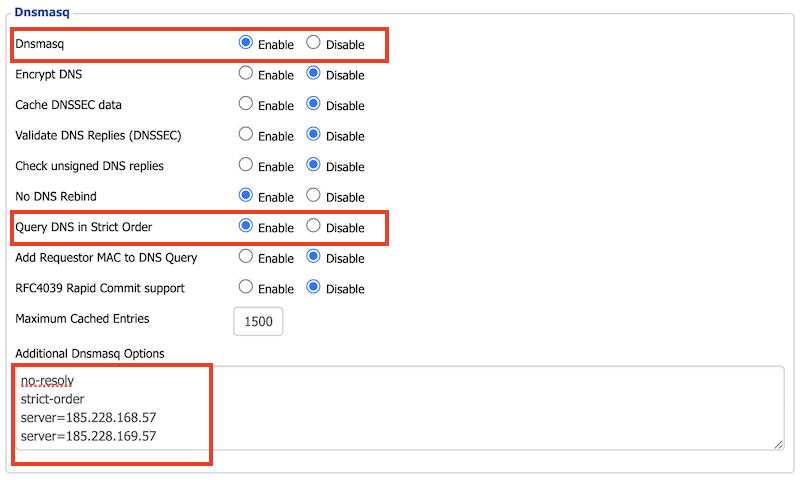
Make sure that Use DNSMasq for DNS and Forced DNS Redirection is enabled.
he last option is important, that is what is going to force all devices on the network to use your preferred DNS. The preferred DNS will be the DNS you select in the sections above.
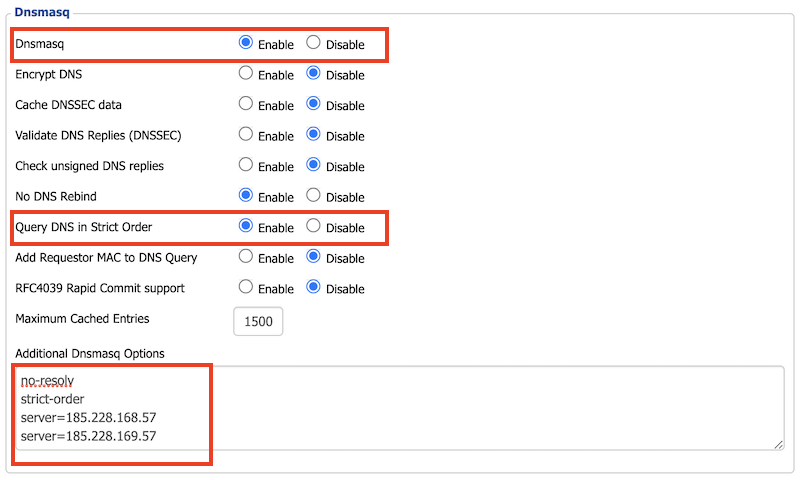
Step 2. Update Services
The last step in the process is to make sure that DNSmasq and Query DNS in Strict Order is enabled.
Lastly, update the Additional Dnsmasq Options with:
no-resolv
strict-order
server=185.228.168.57
server=185.228.169.57Technically, enabling the options above should have forced it but we have found adding the additional options makes it sticky. Use the same IP’s you set up in Step 1.
Lastly, scroll to the bottom of the page. Apply the Settings and for good measure, Reboot Router.
Technically, that should be it. If you update your local DNS settings to another provider, you’ll notice that the machine is responding with responses from the CleanBrowsing router.
In this example, I set the local network to go to the 1.1.1.1 DNS service, and show the response coming from the CleanBrowsing network.
$ nslookup -q=TXT mylocation.whois.dnscontest.cleanbrowsing.org
Server: 1.1.1.1
Address: 1.1.1.1#53
Non-authoritative answer:
mylocation.whois.dnscontest.cleanbrowsing.org text = "CleanBrowsing: dns-edge-usa-central-utah-w, 185.228.169.57"Running a test shows what happens when you pass a site through the network:
$ nslookup pornhub.com
Server: 1.1.1.1
Address: 1.1.1.1#53
** server can't find pornhub.com: NXDOMAIN