CleanBrowsing provides a DNS-based content filtering service, but like most DNS services it is limited by what is happening on the network it is being deployed on. While our system will work to block access to VPN sites, its effectiveness is limited to what the network, and local device, allow.
In this article we provide an example of how to use network devices (like a router) to block VPNs.
What is a VPN?
Virtual Private Networks (VPN) are tunnels that can be created inside your existing network. They create a private environment inside your existing network that opens a window to the outside world ignoring all the restrictions you might have in place. They are especially difficult to work with, and when used have the ability to circumvent almost all attempts to restrict content.
Here is a quick illustration of how it works, we encourage you to read our VPN article for a more exhaustive write up on VPNs:
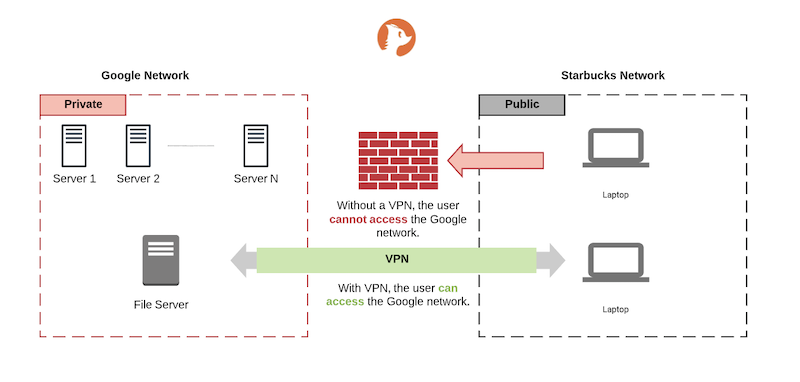
How to disable VPN Access on a Network
VPN’s can be pesky technologies. They are installed in three distinct ways:
- Browsers
- Applications
- Third-party Apps (i.e., AntiVirus)
1 – Disable VPN’s on Browsers
If you are concerned about a VPN you should not allow the Opera or Firefox browsers to be installed. They provide VPN’s embedded into the browser in the name of “privacy”. While great for an adult, it’s a horrible option for a child, someone struggling with addiction, or a number of other use cases. We recommend those browsers be removed and you use your content filter to restrict the ability to install them later.
Additionally, we recommend disabling the ability for a user to install extensions in other browsers like Chrome, Microsoft Edge, and others. Browsers have very large extension, plugin, stores that are full of VPN tools.
2 – Disable VPN’s in Applications
A lot of Anti-Virus applications have VPN’s embedded into the application. We recommend disabling the feature from your devices, restricting it behind an administrators account or switching to a provider that doesn’t include it.
We also recommend taking a proactive approach to hardening mobile devices. The biggest mistake we see is giving a mobile user full control of their device. They have the ability to install whatever they want, when they want and this allows the user to leverage VPN’s and other evasion technologies. The most effective approach to mitigating this is to ensure they don’t have full administrative rights, and leverage parental control features when available.
In addition to being embedded inside an existing application, most VPN’s require the user to download an application to their local machine to work. The easiest way to mitigate this exposure is to a) block access to VPN sites via services like CleanBrowsing, and b) restrict the users ability to install VPN’s in the first place.
3 – Block VPN’s at the Network Level
The most effective way to restrict VPN’s on your network is to do it at your routers firewall. The limitation here will be your technical knowledge and the features provided by your router.
The remainder of this article will show you how to disable VPN’s on your network using a Netgear Orbi router. It’s impossible to account for every router combination, but conceptually the idea is the same. Example: Blocking VPN using Netgear Orbi Router
In most instances the feature you want will be found inside the Advanced or Security menu options, but might be located else where.
Using the knowledge we learned above, we will create a new rule in our router that blocks specific protocols and ports. This will apply to the entire network, which will include every device that connects to it.
In a Netgear Orbi, this is located inside Security > Block Services.
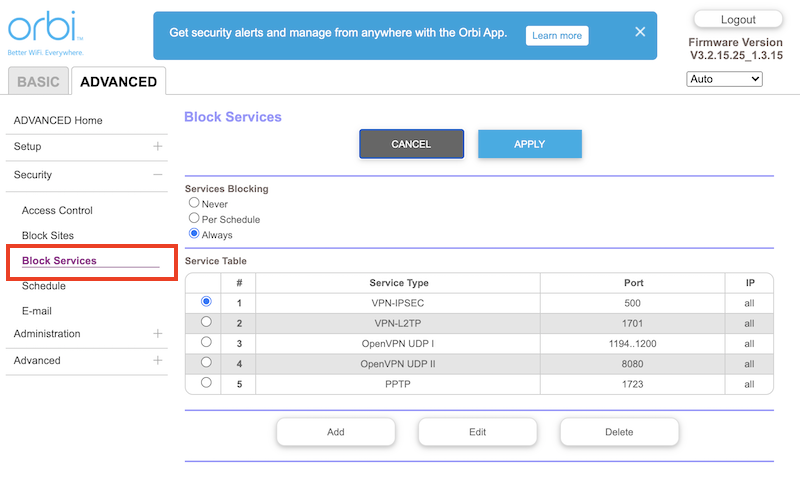
The example shows what the final output will look like. In it, I have added a series of rules, each designed to block a specific Protocol, and port (individual or range). When you don’t know what VPN is being used, it’s best to block the most common options which is what we provided above.
If you do know, you can look up the specific VPN and research the protocols and ports they typically use. Note that the most creative VPN’s, although restricted to the protocols they can use, can get creative with the ports they leverage.
Using the knowledge we learned above, we will create a new rule in our router that blocks specific protocols and ports. This will apply to the entire network, which will include every device that connects to it.
In a Netgear Orbi, this is located inside Security > Block Services.
