During a DNS poisoning attack, a hacker substitutes the address for a valid website for an imposter. Once completed, that hacker can steal valuable information, like passwords and account numbers, or block access to a site.
DNS poisoning is also known as DNS cache poisoning, or DNS spoofing. It is considered a deceptive attack that allows a bad actor to redirect traffic on unsuspecting users. It is often used to push users to fake websites hosted on malicious web servers. They are often used in conjunction with malware-distributing or Phishing websites.
What is DNS Poisoning?
DNS poisoning is a type of spoofing attack that targets DNS infrastructure, specifically DNS resolvers. Via this attack, hackers impersonate another device, client or user. This disguise then makes it easier to do things like intercept protected information or interrupt the normal flow of web traffic.
How Does DNS Poisoning work?
With DNS poisoning attacks, bad actors alter DNS records to redirect users to “spoofed” records that point an unsuspecting user to the wrong location. This usually happens without the users knowledge.
Once the attack is underway, diverting traffic to the illegitimate server, hackers can then accomplish malicious activities like a man in the middle attack (e.g. stealing secure login information for bank websites), installing a virus onto visitors’ computers to cause immediate damage, or even installing a worm to spread the damage to other devices.
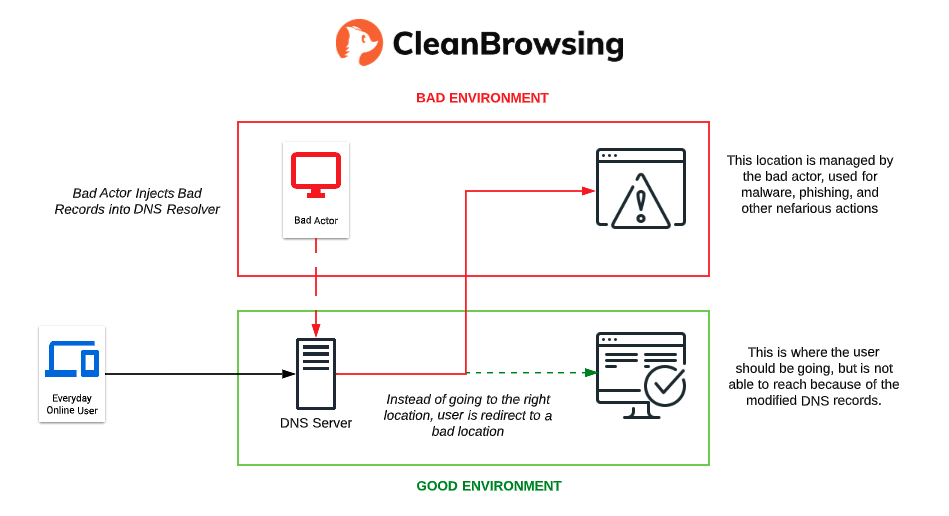
What is the DNS Poisoning Threat?
DNS poisoning allows a bad actor to control what a user can see. This presents an opportunity for three key security concerns:
| Attack | Explanation |
|---|---|
| Malware Distribution | A commont tactic used by bad actors is the distribution of web-based malware like Fake AV Trojans, Rootkits, and other similar payloads. These allow a bad actor to control a users devices, environment. |
| Data Theft | Controlling how data flows allows a user to steal information in transit via Main-in-the-Middle attacks. Malicious servers can perform endpoint termination and see information like usernames and passwords, personal identifiable information, etc… |
| Phishing | Phishing is similar to data theft, but so prevalent it warrants its own call-out. Via a phishing campaign an attacker is able to trick a user to sharing sensitive information while they thing they are on a legitimate website. |
