This article is for technical users. It assumes you understand the mechanics of DNS, and likely manage your own domain zone file. It is specific DNS resolutions issues as they pertain to DNSSEC (good primer on DNSSEC).
If you find that your domain is not resolving across multiple DNS resolvers (using DNSBlacklist.org) like this:
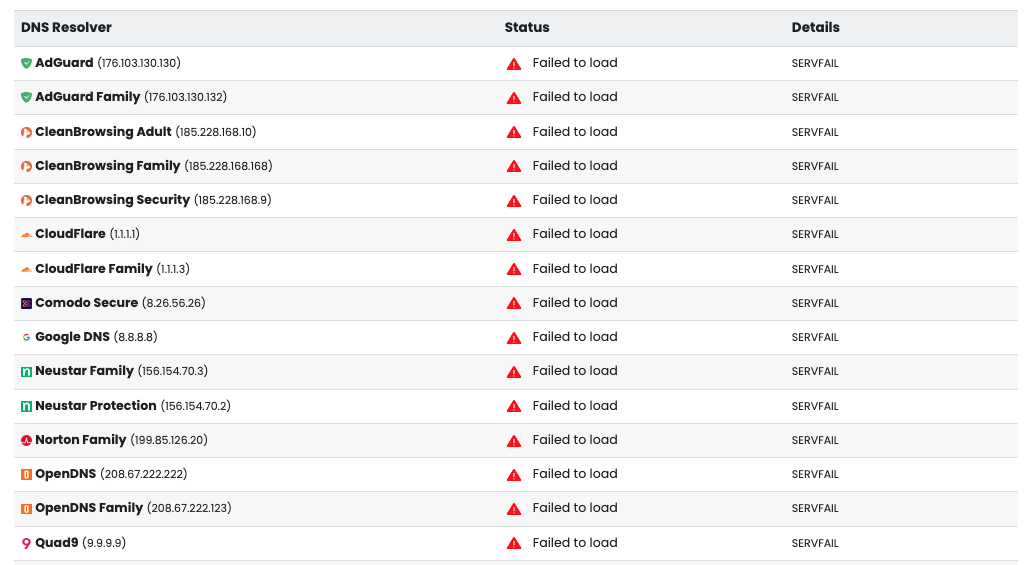
It is in your interest to check domain to see if DNSSEC has been configured, intentionally, or unintentionally. We often find that teams will start the process, but forget to complete or abandon the process and the result is the domain failing to resolve.
There are some simple tools designed to help you troubleshoot:
Both these tools help provide a very simple visualization of what is happening.
Most Common Configuration Issue
The most common issue we see is DNSSEC being configured at the Zone (with your registrar) but not at the DNS level.
Here is what it looks like configured at the zone file with the registrar:
$ dig -t DS dnstests.ovh ; <<>> DiG 9.10.6 <<>> -t DS dnstests.ovh ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 56007 ;; flags: qr rd ra ad; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 1232 ;; QUESTION SECTION: ;dnstests.ovh. IN DS ;; ANSWER SECTION: dnstests.ovh. 172800 IN DS 7645 8 2 1B1B04357A3684E94DBF4406A4052882900BE8FE35014D85E8E873C6 630473D1 ;; Query time: 26 msec ;; SERVER: 1.1.1.1#53(1.1.1.1) ;; WHEN: Fri Sep 02 15:48:15 CDT 2022 ;; MSG SIZE rcvd: 89
The problem stems from the addition of the Domain Signer (DS) record to the domains zone file. This record type is used for the KSK DNSKEY hash for DNSSEC. If a resolver find this record the resolver expects the child-zone to be signed by DNSSEC and will use it to validate.
If the KSK DNSKEY does not exist, the resolver will fail. This will generate something like the following using the Verisign visualization tool:
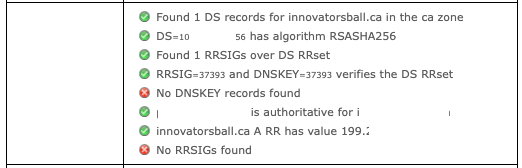
So you can see from the image above, the resolver is looking for the DNSKEY (which does not exist) and RRSIG (which contains the cryptographic signature of a record set.
If it existed, here is what it would look like:
$ dig A +dnssec dnstests.ovh dnstests.ovh. 3600 IN A 213.186.33.5 dnstests.ovh. 3600 IN RRSIG A 8 2 3600 20200925080215 20200826080215 50238 dnstests.ovh. AUz7u4Sq0EkSUq5kR0beowmMuscbzGdb3NI/OhCG8Ow0Z3CqgG0/94eR 6pbG7YJwvCFBU1bQDklLYEfc4mg41VeAVY4xPSv0O76/hEZsVKcBOGlT nKy3wV4ft8ykV1Jl+5q2eJAaZRoBSvHuRItbM2HCyghhDW0gKBy5rqOq BlM=
If it existed, here is what it would look like:
If it for instances appeared like this:
$ dig A +dnssec dnstests.ovh dnstests.ovh. 3600 IN A 213.186.33.5
Where the RRSIG key was missing, it would fail.
In this instance, your best bet is to a) resmove the DS record from your zone file, or b) finish the DNSSEC configuration so that DNS is configured.
